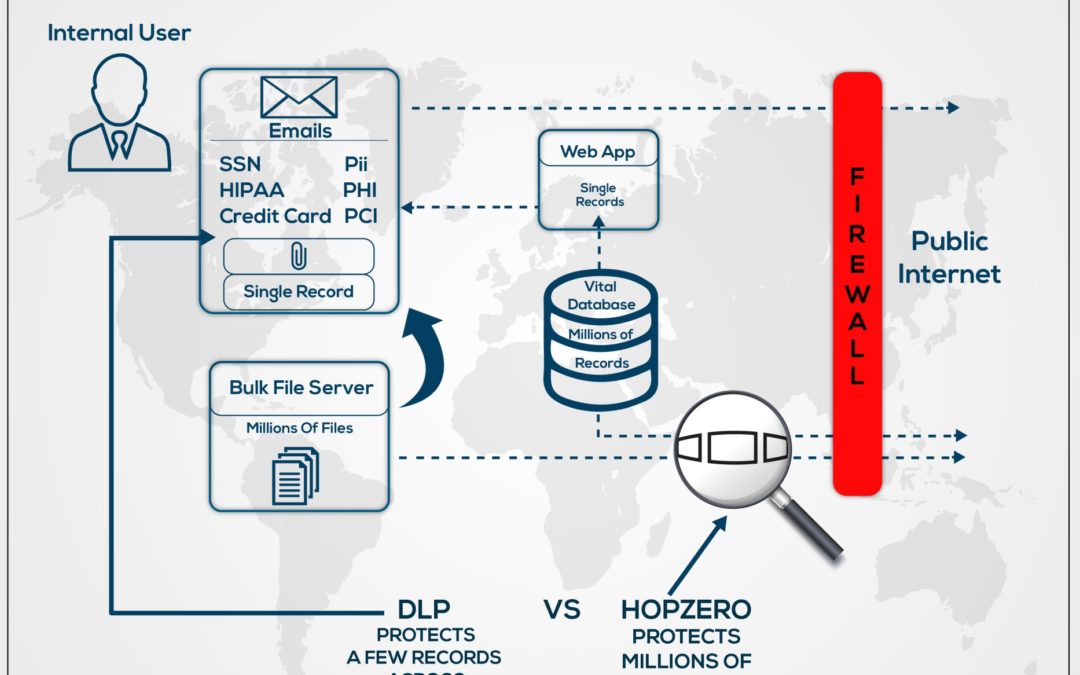
Contrasting Data Loss Prevention DLP With HOPZERO’s Sphere of Trust
HOPZERO protects an entire server database similar to DLP, but for the whole server, preventing data exfiltration by containing DataTravel to a small perimeter.

HOPZERO protects an entire server database similar to DLP, but for the whole server, preventing data exfiltration by containing DataTravel to a small perimeter.

Recent Comments