Here at HOPZERO, considering we have HOP in our name, we believe HOPs are a vital part of the Internet’s architecture, not to mention a powerful way to leverage existing protocols to protect your most-precious data.
But what does this mean for you as a network security professional? How can HOP counts do more for you than just help you pass some certification test? And just what benefit does knowing your data’s HOP counts provide you?
What Does HOP Count Mean?
HOP counts refer to the number of devices, usually routers, that a piece of data travels through. Each time that a packet of data moves from one router (or device) to another — say from the router of your home network to the one just outside your county line — that is considered one HOP.
The HOP count is the total number of HOPs that a packet of data travels. Let’s say you’re on your home laptop and you want to look at the website of the Louvre in Paris. To get all the way from your home office to www.Louvre.fr, you might travel through eighteen routers (or eighteen HOPS) to get to that location. Thereby your packet of data — your request to view this page — will have traveled eighteen HOPs.
Why HOP Count is Important
The reason HOP counts are important is that it only takes, approximately, 40 HOPs for any piece of data to reach the entire world. Yet the default setting for most devices is far higher than 40 HOPs. LINUX has a default HOP count of 64. And Microsoft, since the NT4 Service Pack 6 in 1995, has boosted its default HOP count from 32 to 128.
The reason for these high default HOP counts is user convenience; you don’t want to have to send an email to your colleague in London only to find your email has hit its HOP count limit and isn’t delivered.
The trouble is not all data is created equal. The email you sent to your colleague in London is far different from the customer credit card numbers stored in your data center.
This becomes an even-bigger problem when a hacker or phish gets beyond your firewall — such as when one of your employees mistakenly clicked on a bad link in an email — and that intruder has exfiltrated your data to Bulgaria.
Since it only takes 40 HOPs (or routers) to reach Sofia, the capital of Eastern Europe’s poorest country, and your organization happens to be using Microsoft (with a default hop count of 128), there’s little you can do, once a hacker has breached your sphere of trust, to keep that data from being exfiltrated. No matter how powerful a firewall you may have.
What Does HOP Count Exceeded Mean?
The beauty of HOP counts as a security tool is the fact that there’s a simple protocol that every single router in the world follows. And that is: every time data hops from one router to another the HOP count limit of that data packet is reduced by one. And when that packet hits zero, it automatically destroys itself.
This is a precaution set up for the old BGP routers, a precaution that has protected the Internet for 30 years. For example, let’s say you’re doing some work on your LINUX machine, with a default HOP count of 64. And let’s say you wanted to reach a destination 40 HOPs away. BGP routers always carry a HOP count of 1. Just one.
Well, each router-to-router exchange would decrement the HOP count limit of that data packet by one, from 64 to 63 to 62…and so on. But let’s say you wanted, for some reason, to access a destination that was 65 HOPS away, one more than the default set by LINUX. Well, that data packet would reach just the edge of your intended destination, one router before the device you wanted to communicate with, before that packet would destroy itself. Thereby the packet of data would have exceeded its HOP count.
How Can HOPs Be Used in Network Security?
Okay, but what does this have to do with network security? Well, quite simply, it flips the script on would-be hackers. It allows organizations to be less reactive — waiting for the bad guys to arrive; hoping the firewall holds — and more proactive by setting up HOP limits that serve the best interests of an organization.
Ask yourself this: should your most-precious data — the crown jewels of your company located in your data center — have the same HOP limits that some innocuous emails sent to Europe have? Absolutely not.
Because while that local machine with the innocuous emails might need a heartier HOP limit to conduct business, your crown-jewel data likely doesn’t need a default HOP limit of more than three to five to ensure it stays within the data center. By setting a strict, but appropriate, HOP limit for your most-prized data you ensure it won’t get into the wrong hands, no matter how breached your firewall may be.
How to Measure HOP Count
The trick, of course, is how do you determine what’s an appropriate HOP limit for your varying types of data? Well, first this requires getting a clear look at where your data packets are actually traveling, not just where you think they’re traveling. And then setting appropriate data limits that work within those safe boundaries.
A great tool for discovering where your data is traveling is WireShark. There’s an increasing awareness, and usage of “packet-capture” devices and tools, like WireShark. IT Security engineers have concluded that the protection afforded by firewalls simply isn’t enough. “Knowing your network” means knowing where all your endpoints are communicating to/from. That’s where capture comes into play.
Once you’ve got a clear idea of where your data is traveling, it then becomes a question of analysis. Does my data center with my customer’s private medical data really need a default HOP count of 256? A default HOP count which might allow it to travel to Romania and back? Three times! Probably not.
The HOP count register (also known at TTL) exists in the ethernet packet header of your devices. (See below)
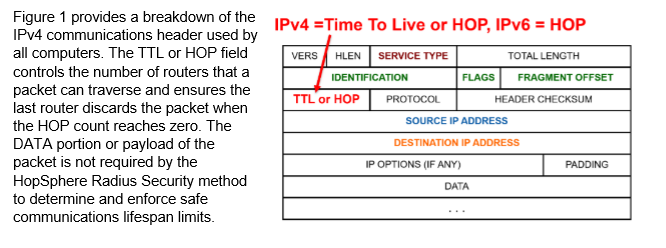 HOPZERO provides a graphical user interface that monitors, tracks, and even “grades” this packet header info for any or all of your network’s devices. “Knowing your network” is the key to being able to set meaningful limits on your data, while simultaneously exposing those devices that are shown to be communicating to places they shouldn’t! We’ll display the time and location of those packet transfers.
HOPZERO provides a graphical user interface that monitors, tracks, and even “grades” this packet header info for any or all of your network’s devices. “Knowing your network” is the key to being able to set meaningful limits on your data, while simultaneously exposing those devices that are shown to be communicating to places they shouldn’t! We’ll display the time and location of those packet transfers.
Here’s a snapshot of our interface:
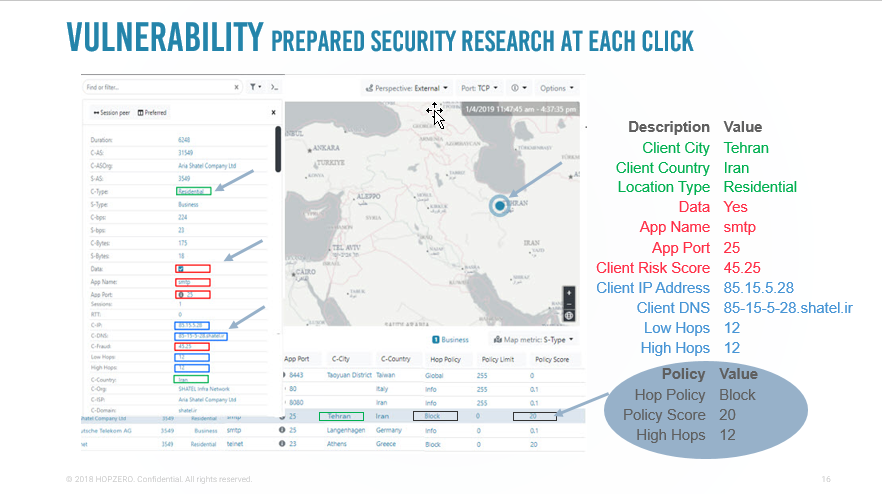
It’s precisely this extraction of critical traffic patterns within your own network, that allows HOPZERO to set up “Secure Radius Zones” protecting your most valuable assets (data).
A Paradigm Shift (or HOP) in Network Security
We may be biased; HOPs, after all, are in the name of our company. But we firmly believe the next real breakthrough in protecting the wholesale raiding of the world’s data will come from enforcing data limits through HOPs.
Instead of trying to build an ever-stronger firewall — that is dependent on factors such as upgrades, updates and the human element — wouldn’t it be better to teach your data to be smarter? To learn where it needs to go and no further? We think so. And we believe if you have a chance to take five minutes to see where your data is traveling — and see HOP security in action — you’ll think so too.




