Security on the Wire
Network Security Intelligence from the Exfiltration Experts
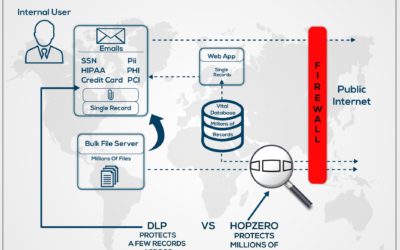
Contrasting Data Loss Prevention DLP With HOPZERO’s Sphere of Trust
HOPZERO protects an entire server database similar to DLP, but for the whole server, preventing data exfiltration by containing DataTravel to a small perimeter.
What Does HOP Count Mean? (and Other Important HOP Questions Answered)
If you’re involved in IT, you’ve probably heard of HOPs. But you might have asked yourself: What does HOP count mean? And why should you care?
HOPZERO Selected as “EMA Vendor to Watch”
Enterprise Management Associates (EMA) is a leading voice in the information security industry. With its dedication to in-depth research — and unrivaled analysis — the EMA is an important resource for data management and IT professionals anywhere. That's why it's with...
HOPZERO Partners With Incubator CTX for Good Cause (and Industry Insights)
HOPZERO & Incubator CTX performed a survey of the enterprise security industry. Most participants opted to donate to Water to Thrive than take a gift card.
CGTN America: HOPZERO Part of “New Silicon Valley”
Why do entrepreneurs choose to live in one state and not another? Is Silicon Valley the "only" viable tech hub? Or are places such as Austin, Texas and Columbus, Ohio positioning to be major players in the next phase of technological innovation? These are some of the...
eWeek: “HOPZERO and ‘Mission Impossible’ – Where Data Self-Destructs”
Your mission, should you choose to accept it, is to find out how HOPZERO’s approach to cyber security is like a Mission: Impossible message…
Why Does Your Server Speak Russian?
We all know how firewalls work; they prevent packets from passing through self-imposed barriers. But they don't limit how far packets go once they pass the threshold. The big question many U.S. organization database managers need to ask themselves is: is my...
Does Your Golden Goose Server Stick Its Neck Out?
Takeaways: Many Back-end “Golden Goose Servers” do Connect to the Internet Firewalls are not the end-all protection they are made out to be It’s dangerous (and expensive) to let your “Golden Goose Server” connect to the entire world A “Golden Goose Server” is a device...
What Could Have Stopped the Most Recent Data Breach?
Takeaways: Prevention is more effective than cure when it comes to network security. Security obviation stops hackers at the source A HOP value limits the amounts of hops that a server takes. It’s a question every consumer and information professional asks...
Legacy Server Security Measures: When Firewalls Fail
Takeaways:Legacy servers, those too cumbersome or expensive to replace, don’t have to be vulnerable to cyber-attack when firewalls fail to protect.Not all firewalls are created equal. In fact, as recent Cisco announcements proved, many firewalls are no longer...