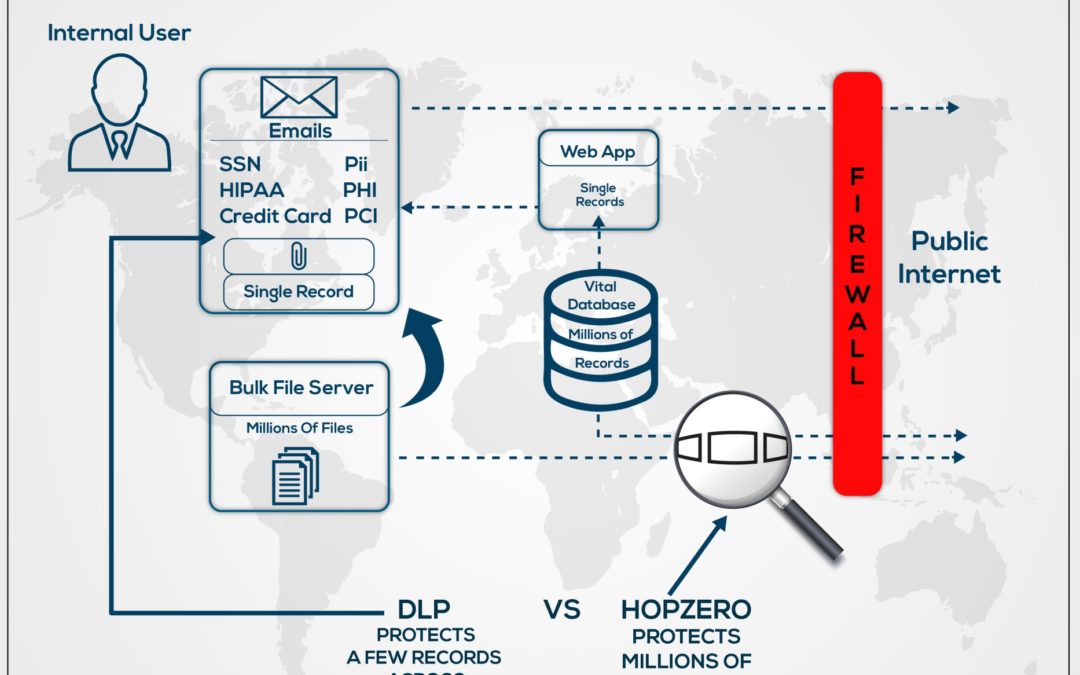
Takeaways:
- Prevention is more effective than cure when it comes to network security.
- Security obviation stops hackers at the source
- A HOP value limits the amounts of hops that a server takes.
It’s a question every consumer and information professional asks themselves: what could have been done to stop the most recent data breach? Just throw a phrase such as “recent data breaches 2017” (or 18…or 19) into Google and you’ll see a continually-evolving list of data breaches affecting some of the biggest brands (and organizations) in the world.
…not to mention a treasure trove of second-guessing and hand-wringing about what could have been done, and what can be done about data breaches in the future!
As with any firewall security issue — and with most things in life — prevention is far more effective than any network security cure. In this article, we’ll discuss a most-powerful remedy for safeguarding your organization’s most precious information assets, and how it could have been used in the most recent data breach.
The Most Recent Data Breach Didn’t Have to Happen
Picture if you will: A puppy runs toward the path of a semi-truck – as disaster looms, a choker chain limits the movement of the dog, saving the pup. In a similar way, HOPsphere Radius Security limits data exposure outside the data center. It’s like a choker chain on server packets, limiting communications – obviating data compromise — and providing security when you need it most…before a cyber-attack occurs.
“It’s like a choker chain on server packets, limiting communications – obviating data compromise.”
[VIDEO] Discover How HOPZERO Can Help
What does “obviation” mean? Security Obviation can be categorized as a capability that stops a hack before it happens.
- Hackers can’t even get a login prompt
- HOPsphere Radius Security stops continual, faraway hack attempts from the deep web
- Unsophisticated hackers (script kiddies or terrorists) intent on harm are frustrated and thwarted
Our own National Security Agency (NSA) developed hacking tools, themselves compromised, that now provide hackers automated methods to seriously compromise systems, of almost any size.
The preponderance (80%) of the sources of those hacks are from faraway, remote countries termed the “deep web.” Thousands of these scripts run 24 hours a day, aimed at high-value targets from deep web hackers.
Many network professionals are lulled into a false sense of security, thinking firewalls will be the ultimate line of defense. Every hacked organization had firewalls standing by the castle. And all Cisco firewalls can be compromised by recently-compromised NSA tools, if not updated recently.
Expensive security products engage the hack attempt, identify it, log and report it, then mitigate the attack.
HOPsphere Radius Security also helps prevent database compromise, preventing hackers from even getting a login prompt. This keeps the database safe inside the datacenter and, when used in conjunction with sophisticated security products, it can save millions of dollars by obviating faraway nuisance attacks that consume firewall processing and manned operations research.
HOPvalue settings place databases in stealth mode outside the limited HOPsphere.
The Power of a HOPvalue
A server’s HOPvalue limits the number of router hops a server’s packets can travel before being discarded. The HOPvalue is the choker chain for high value server data, limiting server packets safe inside the data center.
HOP=default, starts as high as 255 router hops, allowing dangerous unlimited worldwide communications. With the HOP limit starting lower, it’s like running out of fare on the tollway: routers discard packets when time-to-live HOP=0. Imagine a router as a toll taker, decrementing fare or -1 HOP through each router until the packet is discarded after reaching zero (0). For instance, if HOP=4, packets can only traverse three routers before packets expire and are discarded.
Here are some example HOP values to achieve limits. (Actual HOP needs to be analyzed from location)
- HOP=1 No routing
- HOP=4 No communications outside the data center.
- HOP=8 No communications outside an internal network
- HOP=12 No communications outside a regional area
- HOP=15 No communications outside a state
- HOP=18 No communications outside the nation
- HOP=22 No communications outside developed countries
HOP=default values of 64, 128, 255 allow dangerous, unlimited worldwide communications enabling hackers around the world to hack systems 24/7.
Each packet starts out with a HOPvalue, up to 255 router hops. As packets traverse routers, HOP value is decremented by one (-1). Once routers decrement the HOPvalue to zero, they discard the packet, stopping it from continuing. Microsoft uses HOP=128 as default value, but each device can be configured between 0-255. Its original purpose was to prevent packets from spinning in a loop, indefinitely consuming bandwidth and resources. By using this feature to starve the HOP, setting it lower than its default, it limits the radius of communications. If HOP=4 a server’s packets can traverse only four routers and be discarded.
HOPsphere Radius Security uses the knowledge and power of network theory existing in every network device and router. Prevention is accomplished by setting the HOP value; HOP=x where x=max number of router hops inside the datacenter.
After applying, hackers cannot directly connect to the database outside of the datacenter. Neither inside users nor outside Internet users can communicate with the database, because packets from the database expire at the border of the datacenter. Even if firewalls were to allow communications, HOPsphere Radius Security settings prevent packets from leaving the data center.
Example. If the datacenter has a maximum of three router hops from end to end, the HOP set on the database is set to HOP=4, meaning packets sent from the database would start with HOP=4. The first router would decrement by one down to HOP=3, the second router would decrement HOP=2, the third router would decrement HOP=1 and the fourth router would stop and discard the packet from further communications as the HOP=0, preventing any further communications.
With the database set HOP=4 no devices further than four router hops can communicate with the database. With or without a firewall, the database can only send through four routers before its packets expire and are discarded.
The HOP=4 setting can be set from its default value which is typically 64, 128, or 255, depending on the database platform used. Microsoft uses 128 and Unix variants are 64 or higher. The setting requires root or administrator credentials to change the setting, and sometimes requires a restart to enable the setting. Once set, the device, because of the way routers operate, will not allow packets to travel through more than four routers Dynamic Host Configuration Protocol (DHCP) set HOP by using Option 23 to HOP=x. HOP settings can be accomplished using DHCP, making it even easier without having to change the device settings directly. The device can be set by DHCP Reservation so it receives the same IP address and options each time.
Databases typically only transact with middleware, web or application servers which are inside the datacenter. Databases also need access to LDAP, AD, and NTP for security and time settings, which are also inside the datacenter.
HOPsphere Radius Security protects databases from transacting with devices outside the HOPsphere setting, while enabling communications with appropriate devices inside the HOPsphere.
Hackers cannot get so much as a login prompt to use lost or stolen credentials or use credential cracking methods.
This security layer is highly effective stopping internal users or Internet users from identifying the device, as port scanning does not respond to scans. This prevents the hacker from even knowing the device exists with an ICMP Ping or Application Port, because the response packet expires and is discarded by routers. Hackers cannot get so much as a login prompt to use lost or stolen credentials or use credential cracking methods.
Consider these other benefits of HOPsphere Radius Security:
- This solution: Stop database compromise
- Stop hacker inside pivot point acquisition
- Stop IoT (e.g., cameras) use as pawns in Denial of Service attacks
- Stops access to medical or biomedical equipment
- Stop access to systems using lost or stolen credentials
- Stop hacking of web servers from far away hackers in foreign countries
- Stop email spam from far away hackers in foreign countries
- Stop browser users from web malware far away hackers in foreign countries
- Stop Trojan software from connecting/dropping data to hackers in foreign countries
- Stop internet-facing routers/switches/balancers from attempted login by hackers in foreign countries
- Stop unpatchable legacy devices from being attacked inside network or from the Internet, or from, hackers in foreign countries
- Stop frivolous script kiddies from overwhelming firewalls, load balancers and sophisticated security products, enabling security devices to apply greater granularity and fidelity to real attempts
- Hide devices from being attacked or even being identified by hacker’s scans from beyond the rule of law
- Force hackers to expose their attacks to “within the rule of law” realms, where ISPs and law enforcement can trace and stop sources of attack more effectively.
- Move focus to obviation security (not allowing attempts) instead of identifying, preventing, and reporting on attempts. Casual hackers move on when they can’t validate device existence, and are forced to move closer where the rule of law can enforce.
How We Can Help
HOPZERO can help safeguard your information technology from some of the same threats that caused the most recent data breach, schedule your own FREE in-house consultation.