How Hopzero Sphere of Trust Works
Contain threats before they spread by controlling the fundamental travel distance of data: packet lifetime.
Built on TTL: Time-to-Live as a Containment Tool
Every packet in an IP network has a time-to-live value—a counter that decreases with every router hop. When it reaches zero, the packet is dropped. Hopzero reclaims this overlooked field to create real containment zones.
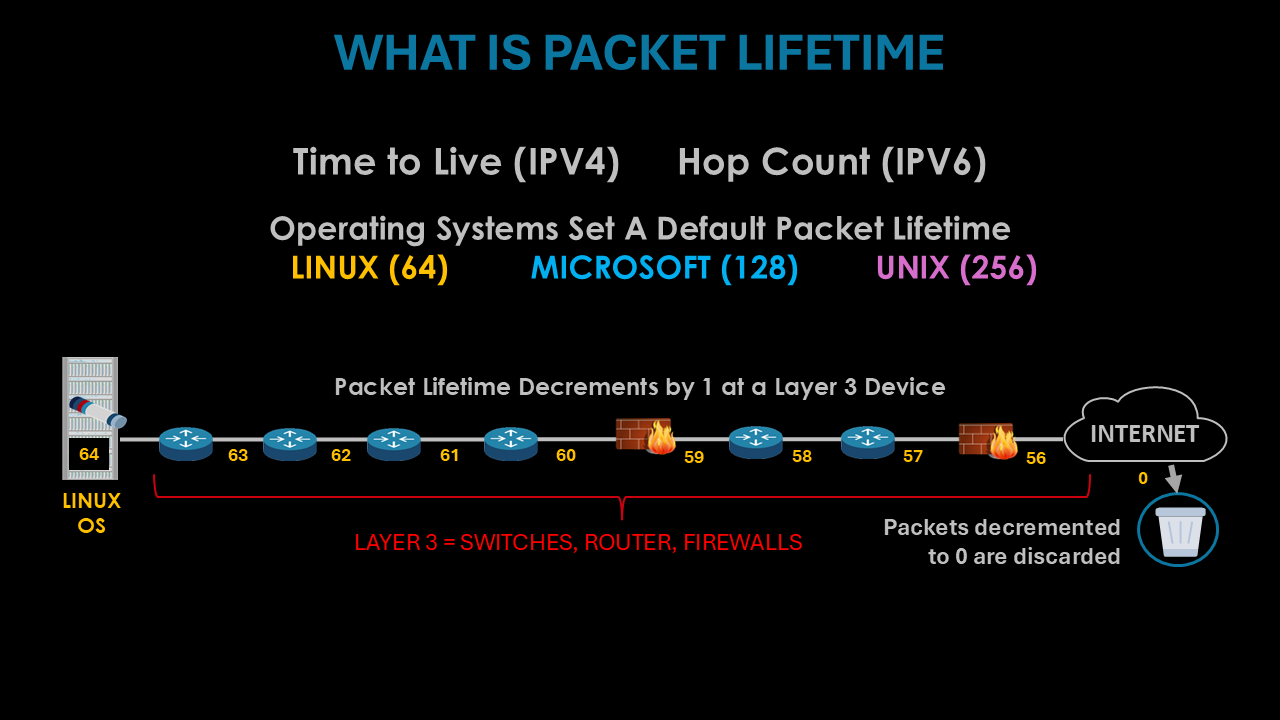
Packet lifetime, also known as TTL or HOP Count is an 8-bit value in a packet header that signifies how long the packet can exist in the network. It prevents lost packets from being routed forever and creating congestion on the Internet. This slide illustrates how packets have a lifetime causing it to be discarded when it decrements to 0.
Hop-by-Hop Enforcement for Containment
Endpoint Agents
Set TTL values on outgoing packets based on policy
Gateways
Inspect TTLs and reject out-of-bound traffic
Switch Port Policy Injection
Allows TTL rules to be enforced without endpoint control
This creates a network-wide enforcement mesh—unbreakable by attackers, invisible to users.
Containment Capabilities
Packet Lifetime Containment
Define the reach of every device or application in hops.
Network Geo-Fencing
Prevent data from escaping regions or cloud zones.
Application Tethering
Keep apps tethered to only their approved resources.
Man-in-the-Middle Detection
Detect path manipulation through TTL deviation.
Micro-Segmentation
Enforce Zero Trust zones without complex VLANs or firewall rules.
Visualizing Hopzero Containment
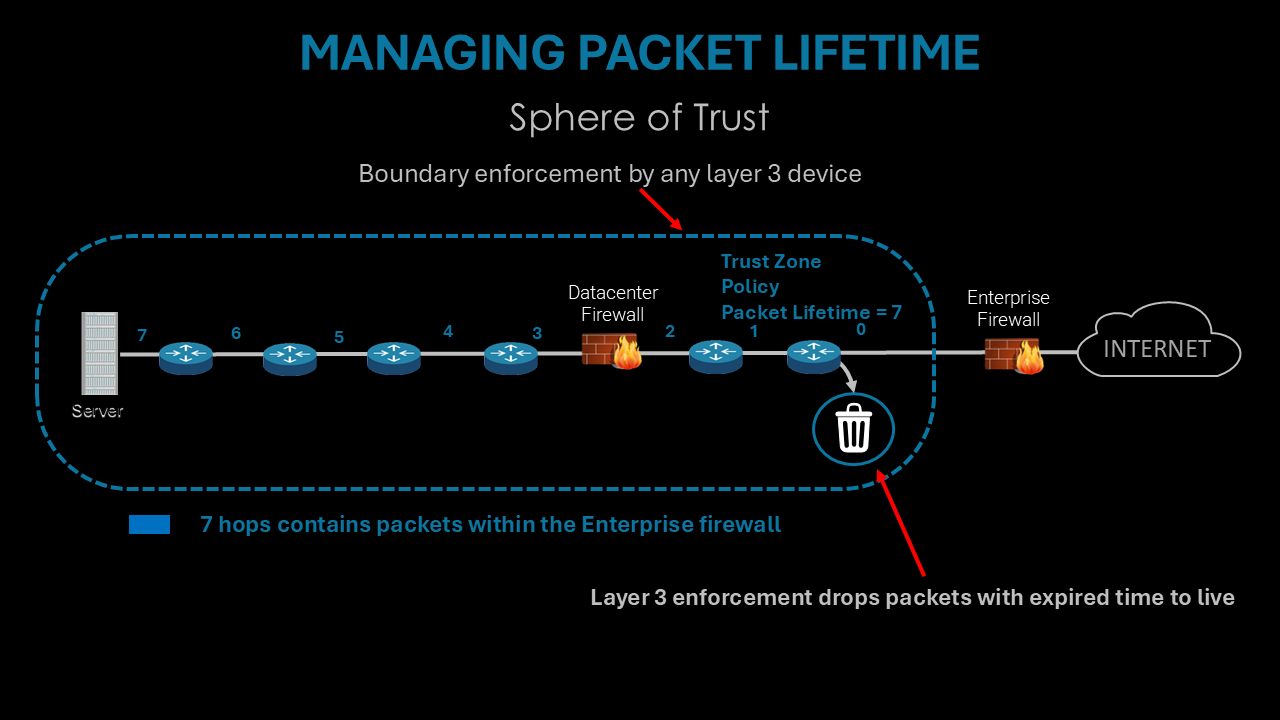
Hopzero Sphere of Trust manages packet lifetime by Protocol, Application Port, IP Source and IP Destination creating Sphere of Trust Micro-Segmentation around each application packet.
Seamless Integration. Modular by Design.
Hopzero’s lightweight, modular codebase is built for flexibility — enabling effortless integration into a wide range of security solutions, from NDR and XDR platforms to firewalls and cloud-native stacks. Whether you’re deploying at the edge, in the cloud, or across hybrid environments, Hopzero adapts to your architecture without friction.
Deployment Options:
Modular Enforcement Plugins
Deploy as a lightweight agent, embedded gateway shim, or inline sensor — each designed to enforce packet lifetime without impacting performance or requiring endpoint installation.
Inline Path Control
Integrate via SDN hooks, virtual TAPs, or Layer 3 switches to enable active hop-limit enforcement — ideal for real-time segmentation and zero-trust boundaries.
Cloud-Native Agents
Add enforcement to cloud workloads with agent-level TTL control, ensuring secure isolation across VPCs, containers, and hybrid clouds.
Passive Integration with Alerting
Run in monitor-only mode for seamless alert generation via your existing SIEM, NDR, or log aggregation tools. Perfect for proof-of-value, risk assessments, or staged rollouts.
