Explore the Technology Behind Hopzero Sphere of Trust
Uncover the innovative enforcement methods that contain threats before they propagate—with patented TTL-based security.
Technology Focus Areas
Packet Lifetime Enforcement
Set and enforce TTL limits on outbound traffic based on trust policies.
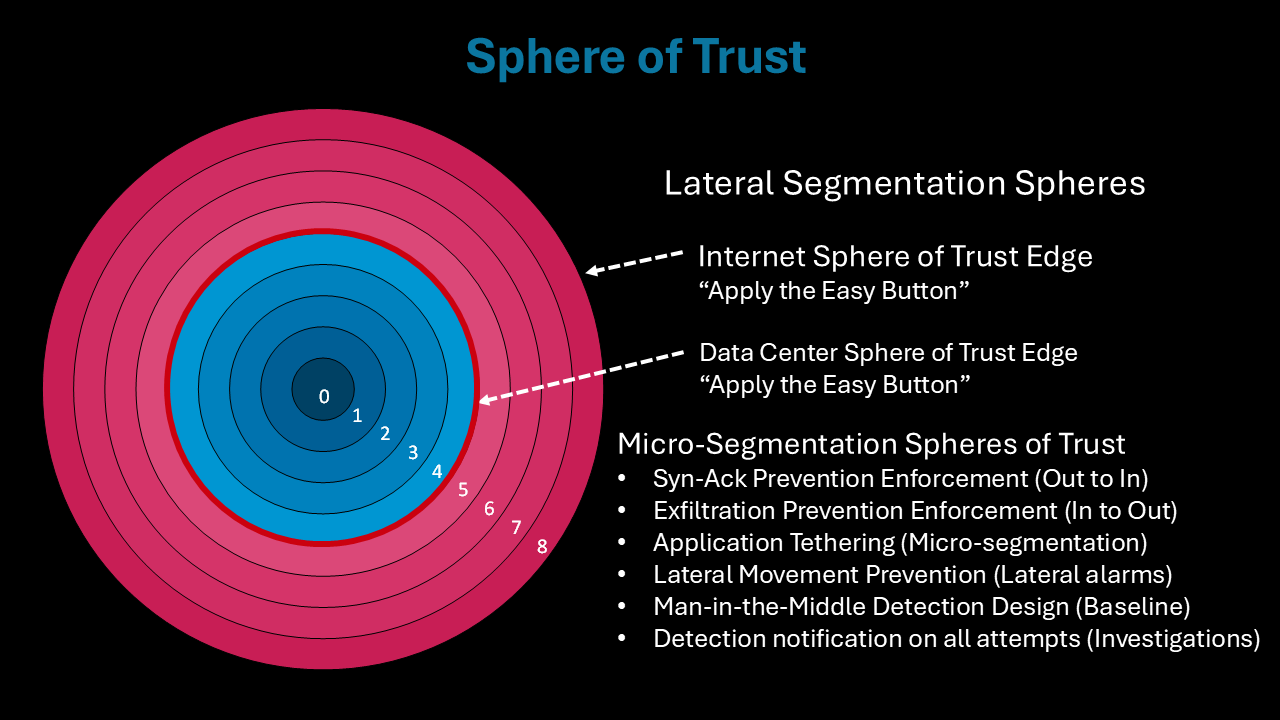
Distance-Based Micro-Segmentation
Create Zero Trust boundaries without relying on VLANs or firewalls.
Network Geo-Fencing Without GPS
Prevent sensitive data from crossing into unauthorized regions or cloud zones.
Application Tethering
Tie apps to fixed zones, isolating them from lateral or C2 access.
Passive MITM Detection
Monitor TTL deviations to detect unauthorized middleboxes or spoofed routes.
TTL-Based DLP
Ensure critical data cannot exit approved security zones—even if credentials are compromised.
Architecture & Enforcement Pathways
Sphere of Trust works across three architectural modes:
Agent-Based
Local TTL enforcement on endpoint packets before they reach the wire.
Gateway-Based
Policy validation at secure traffic inspection points.
LAYER 3 DEVICE INJECTION
TTL rules assigned dynamically at the Layer 3 ports
